In this release we have updated the Hypernode platform with new NGINX rules to block an attack on the Magento Page Builder. Last month with the Magento 2.3.3 and 2.2.10 Security Update a patch was released for a Remote Code Execution (RCE) vulnerability in the Page Builder:
PRODSECBUG-2403: Remote code execution through crafted Page Builder templates – CVE-2019-8144
Description: An unauthenticated user can insert a malicious payload through Page Builder template methods.
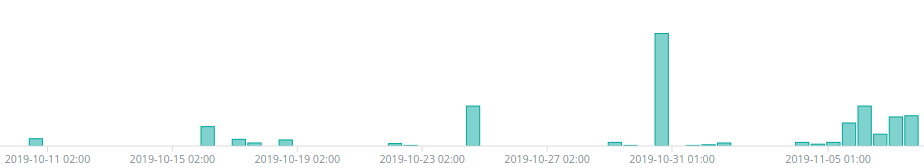
Now a month later we’ve seen signs of abuse of this vulnerability in the wild. We’ve noticed suspicious probes on our platform for a related endpoint as early as 10-10-2019, with a surge on Halloween and an increasing amount of probes in the past couple of days, mostly coming Ukrainian and Swiss IPs.
As a preventive measure we’ve deployed NGINX rules to block the probed endpoint on all Hypernodes that got scanned and firewalled IPs that we’ve seen scanning for this vulnerability. Today we’ll deploy WAF rules on all other Hypernodes for this vulnerability as well. If this breaks Page Builder functionality for you, you can edit the NGINX config in /data/web/nginx in order to whitelist safe IPs or to remove the block when you’ve updated to Magento 2.3.2-p1, Magento 2.3.3.
Note that while server-side WAF rules may block an initial wave of attacks, it is still important to patch your shop as hackers are known to get creative and there might be other ways to perform the same type of exploit.